Protecting video content has become paramount for creators and distributors. With the increasing threat of unauthorized access and sharing, securing video streams is not just a preference but a necessity. This article delves into using signed URLs to secure video content, drawing insights on video protection and using signed URLs.
What are Signed URLs?
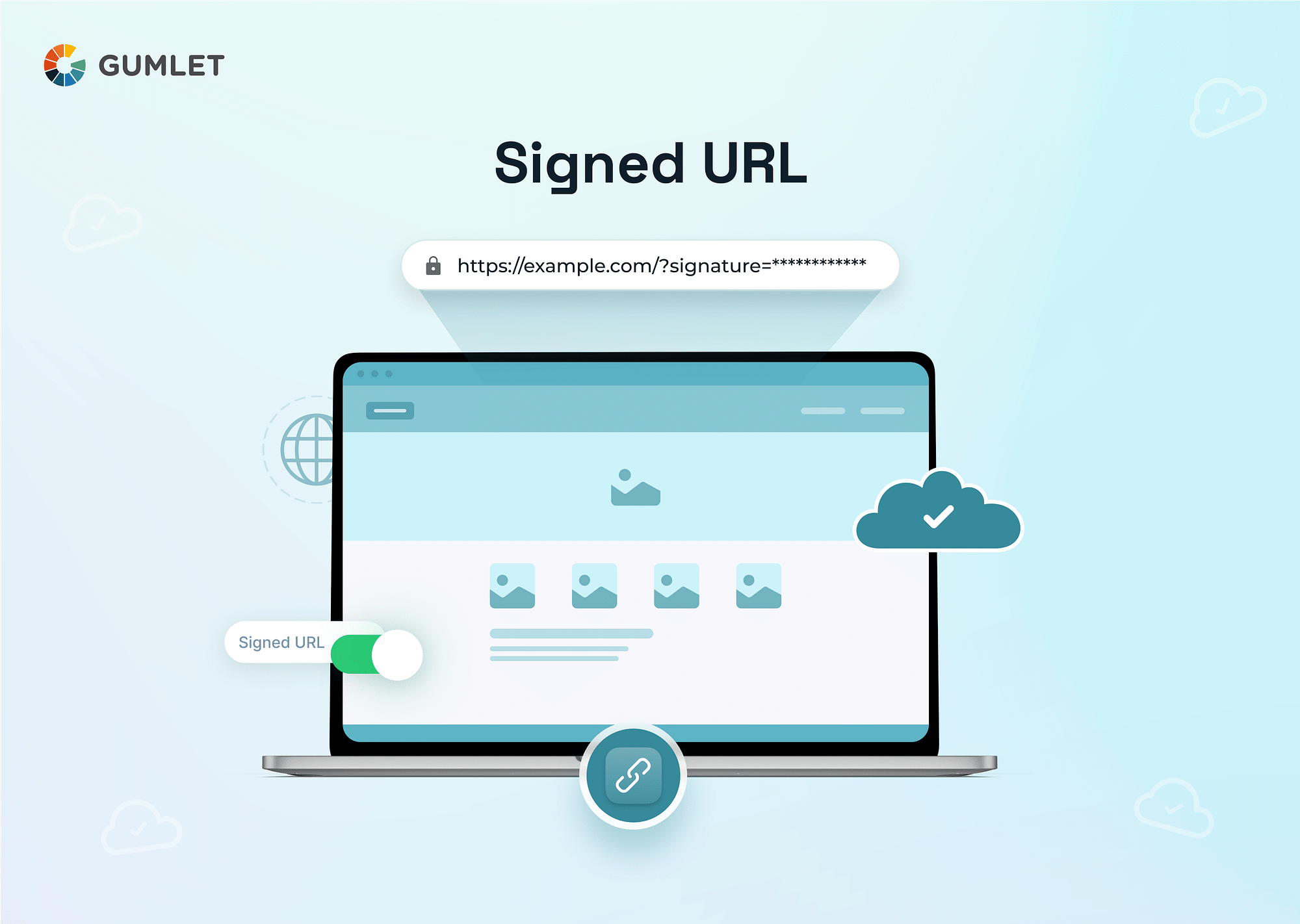
Signed URLs represent a sophisticated yet essential method in the realm of online content protection, particularly in securing video streams. Fundamentally, a signed URL is a standard web address that has been appended with an additional encrypted signature. This signature, unique to each request, is the cornerstone of its security mechanism. It's created through a cryptographic algorithm, using a secret key known only to the content distributor.
The role of signed URLs in secure video streaming includes:
- Authentication and Authorization: The encrypted signature in a signed URL ensures that a video stream can only be accessed by users who have received this URL legitimately. This process effectively authenticates the user and authorizes their access.
- Prevention of Unauthorized Access: Since the signature is unique and often time-bound, it becomes nearly impossible for unauthorized users to access the content by guessing the URL or using a URL they obtained illicitly.
- Content Security: For content creators and distributors, especially in the video domain, controlling who can view the content is crucial. Signed URLs provide a way to keep the content secure and accessible only to paying customers or authorized viewers.
- Flexibility and Control: Content providers can set various parameters in a signed URL, such as expiration time, IP address limitations, or access rights. This level of control is particularly important for video content, which may have different viewing rights based on geography or user subscription level.
Key Features of Signed URLs
Signed URLs are instrumental in securing online content, especially videos, by offering several key features that enhance security and control. These features include:
- Content Integrity and Authenticity: Ensures that the content is not tampered with and remains as the creator intended.
- Limited Access and Time Restriction: Access to the content is restricted to a specific time frame, reducing the risk of unauthorized sharing.
- Enhanced Protection Against Unauthorized Sharing and Access: Provides a robust barrier against unauthorized users, safeguarding the content.
- Scalability and Flexibility for Different Use Cases: Adaptable to various content types and user scenarios, making it a versatile solution.
Application of Signed URLs in Video Security
The application of signed URLs in video security is a game-changer, addressing multiple challenges in content protection and video distribution. These applications include:
- Controlled Access: Signed URLs ensure that only intended audiences can view the video content, safeguarding against unauthorized viewing.
- Prevention of Piracy: By limiting access, signed URLs play a crucial role in combating video piracy and protecting revenue streams for content creators.
- Secure Distribution: Facilitates safe and controlled distribution of video content across platforms, maintaining content security throughout the distribution chain.
Signed URL vs. Pre-signed URL
In the context of video security and content management, understanding the distinction between signed URLs and pre-signed URLs is crucial. Each serves a specific purpose and offers different benefits. Here's a comparison in a tabular format, focusing on their application in video streaming:
| Aspect | Signed URL | Pre-signed URL |
|---|---|---|
| Definition | A URL that includes a cryptographic signature as a query parameter, generated dynamically for each request. | A URL that is pre-generated with a signature, often used for temporary access to a resource like a file in a storage bucket. |
| Usage in Video Streaming | Commonly used for secure, on-demand video streaming, where each request is uniquely validated. | Often used for providing temporary access to stored video files, like in cloud storage services. |
| Security Level | High, as it allows for real-time validation and can include user-specific data in the signature. | Moderate, as it's typically time-bound but not user-specific. |
| Flexibility | Highly flexible, can integrate advanced security features like IP restrictions and access rights. | Less flexible, generally limited to time-based access control. |
| Complexity of Implementation | More complex due to dynamic generation and validation of signatures. | Simpler as the URL is generated once and can be used until it expires. |
| Control Over Access | Greater control, allowing for detailed and varied access parameters per user. | Control is mainly limited to the duration of access, with fewer customization options. |
| Ideal Use Case | Best for scenarios where highly secure, controlled, and user-specific access to video content is required. | Suitable for scenarios where temporary, less personalized access to videos is sufficient. |
Step-by-Step Implementation of Signed URLs for Video Security
Implementing signed URLs for video security is a strategic process that ensures the safeguarding of video content from unauthorized access. Gumlet, a video hosting and video optimization platform, utilizes signed URLs to enhance video security. Here’s a step-by-step guide to implementing signed URLs:
- Generate a Secret Key: The first step involves creating a secret key, unique to your organization. This key is the foundation of the security process, as it will be used to generate the encrypted signature for the URLs. In Gumlet's context, this secret key is securely stored and managed within their platform.
- Set Expiration Time: Determine how long the URL should be valid. This is crucial for video content, as it prevents long-term unauthorized access. With Gumlet, you can set flexible expiration times based on your content strategy and security needs.
- Construct the Signed URL: Combine the original URL of your video content with additional query parameters that include security and access information. In Gumlet’s system, this process is streamlined to ensure that the URL construction adheres to best practices in security and efficiency.
- Generate the Signature: Using the secret key, generate a cryptographic signature that will be appended to the URL. This signature is unique for each URL and is based on the combined data of the URL and the secret key. Gumlet's technology ensures that this signature is robust and conforms to high-security standards.
- Integrate and Validate Signed URL: Finally, integrate these signed URLs into your video delivery system. Validation is crucial to ensure that the URLs function as intended, granting access to authorized users and denying it to unauthorized ones. With Gumlet, this integration is designed to be seamless with existing video delivery workflows, ensuring minimal disruption and maximum security.
By following these steps and leveraging Gumlet's technology, businesses can effectively use signed URLs to protect their video content. This approach not only enhances security but also offers scalability, making it suitable for a wide range of applications and business sizes.
Performance Optimization with Signed URLs
While signed URLs are crucial for video content security, it's important to understand their impact on performance and how to optimize it. Here's a brief exploration:
- Impact on Delivery Speed: Implementing signed URLs can slightly increase the time it takes to validate each request, potentially impacting video delivery speed. However, this impact is usually minimal and often outweighed by the security benefits.
- Content Delivery Network (CDN) maintain Usage: Integrating a CDN can significantly improve delivery speeds. CDNs can handle the distribution of encrypted content efficiently, ensuring that the security added by signed URLs doesn't hinder performance.
- Optimize Signature Generation: Optimize the algorithm for signature generation to be as efficient as possible. The quicker the signature is generated, the lesser the impact on overall response time.
- Regular Monitoring and Adjustments: Continuously monitor the performance and make necessary adjustments. Regularly reviewing and tweaking the system helps maintain an optimal balance between security and performance.
FAQs:
What is a signed and unsigned URL?
A signed URL has an encrypted signature for security, while an unsigned URL does not have this layer of protection.
What is a signed URL example?
A video link that includes a unique signature in its query parameters for restricted access.
Is this implementation of signed URLs reasonably secure?
Yes, when correctly implemented, signed URLs provide a strong level of security.
Can I increase the expiration time on the signed URL?
Yes, the expiration time can be adjusted based on the specific requirements of the content.